Hashing is a fundamental concept in cryptography that is widely used in a variety of technologies including password storage, data integrity, digital signatures, and blockchain. Hashing is used in blockchain to ensure the integrity and security of data stored in the chain.
This article will look at the concept of hashing and how it is used to ensure data integrity in blockchain technology.
Blockchain Technology
Blockchain technology is a distributed digital ledger that is decentralized and used to record transactions across multiple computers. It is a safe and transparent method of storing and sharing data across a network.
A blockchain is a chain of blocks, each of which has a list of transactions in it. These transactions can be anything from financial transactions to digital contracts to simple messages. The blocks in the chain are cryptographically linked to one another, resulting in a secure and unchangeable record of all transactions.
Decentralization is another important aspect of blockchain technology. In contrast to traditional centralized systems, where a single entity controls and manages the data, the data in a blockchain network is stored and maintained by multiple entities known as nodes. Because of this decentralized architecture, blockchain networks are extremely resistant to tampering, fraud, and hacking.
Blockchain technology is also highly transparent, as all network transactions are public and every node has a copy of the full blockchain. This transparency ensures that all network transactions are traceable and auditable.
Many possible applications for blockchain technology exist, including financial transactions, supply chain management, digital identity, and many others. The technology is still in its early stages, and many organisations and businesses are looking for ways to use it to better their operations and services.
Hashing
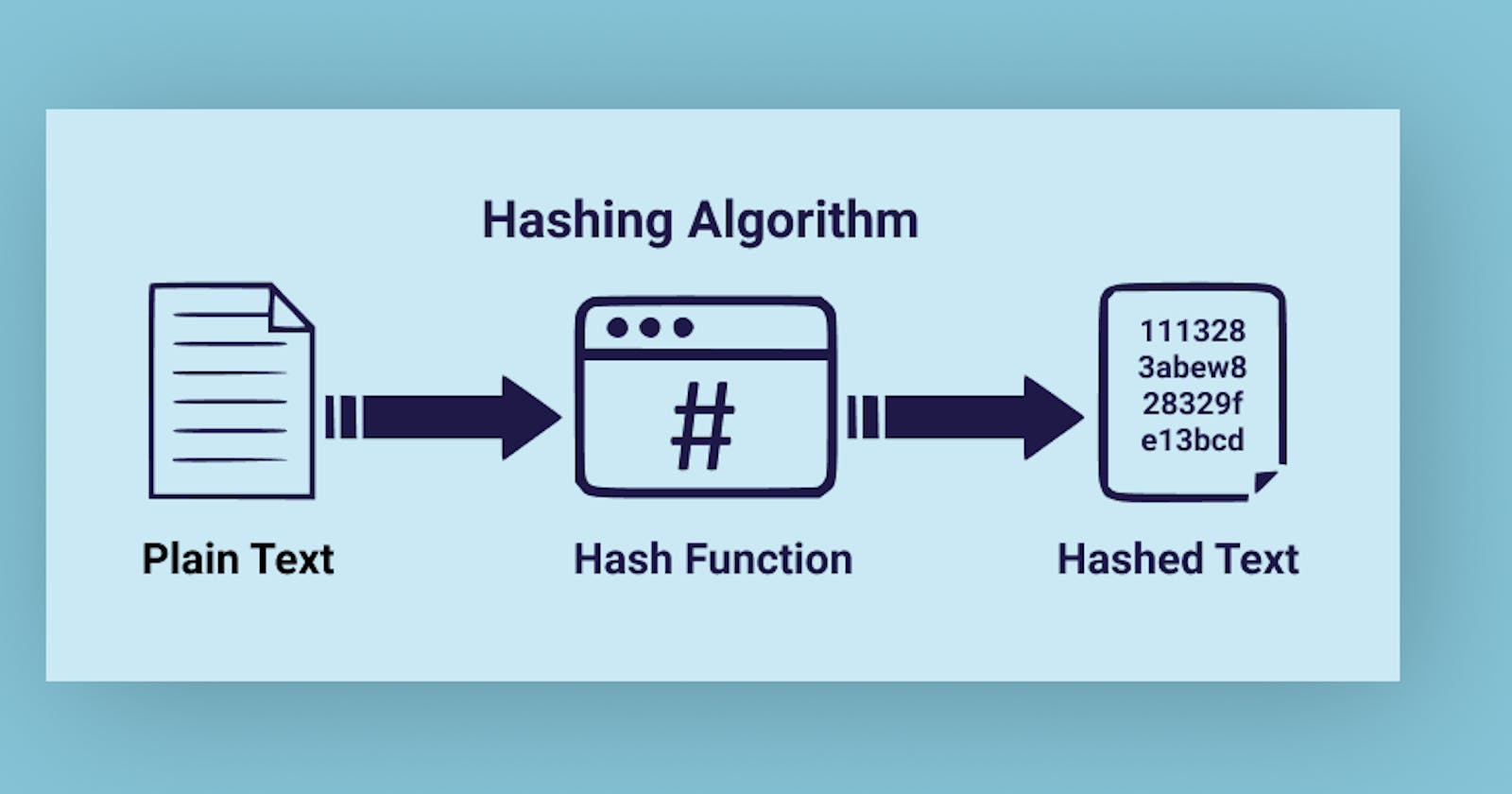
Hashing is the process of converting a string of characters into a fixed-size output for security purposes. Although the phrases hashing and encryption are frequently used interchangeably, hashing is always used for one-way encryption, and hashed values are extremely difficult to decode.
The process of hashing is deterministic and it is not possible to reverse the process and obtain the original input from the hash. Hashing algorithms are mathematical functions that take an input and produce a hash, which is a fixed-length output. Hashing is used for many things, including password storage, digital signatures, and data integrity.
For example, in password storage, the password is hashed before being saved in the database, so even if an attacker has access to the database, they will not be able to obtain the original password. Hashing is also used in digital signatures to confirm the message or document's legitimacy.
Hashing in Blockchain Technology
In blockchain technology, hashing is used to ensure the integrity of data stored in the chain. Each block in the blockchain contains a unique hash that is generated from the contents of the block. The hash of a block is generated by applying a hash function to the contents of the block, which includes the list of transactions, the hash of the previous block, and a random number known as a 'nonce'.
The purpose of the hash of a block is to ensure the integrity of the data in the block. Since the hash is generated from the contents of the block, any change to the data in the block will result in a different hash being generated. This means that if someone tries to tamper with the data in a block, the hash of the block will no longer match the one that is stored in the chain, and the tampered block will be rejected by the network.
The linking of each block's hash to the hash of the previous block creates a chain of blocks that is extremely difficult to change. Because each block in the chain contains the hash of the previous block, any change to a block in the chain will affect all subsequent blocks, and the network will reject the entire chain.
Furthermore, using a nonce in the hash function gives an extra layer of protection. A nonce is a random number that is used in the hash calculation. If a malicious actor attempts to change the contents of a block to generate a new valid hash, they must also find a new nonce that produces the same hash. This computationally demanding task would necessitate a substantial amount of computational power.
Data Integrity
Data integrity refers to the accuracy and completeness of data over its entire lifecycle. It ensures that data is not tampered with, altered, or corrupted, and that it remains consistent and reliable.
In the context of blockchain technology, data integrity is achieved through the use of cryptographic hashing. Each block in the blockchain contains a unique hash that is generated from the contents of the block. The hash of a block is used to ensure that the data in the block has not been tampered with, and any change to the data will result in a different hash being generated.
In a blockchain network, every node has a copy of the entire blockchain and all transactions are publicly visible. This transparency ensures that all transactions on the network are verifiable and auditable, further enhancing the data integrity of the blockchain network.
Data integrity is a crucial aspect of blockchain technology. The use of cryptographic hashing and the linking of each block to the previous block ensures that data in the blockchain is accurate, consistent, and reliable and that it cannot be tampered with. The transparency of the network also ensures that all transactions are verifiable and auditable, providing an additional layer of security and trust.
Conclusion
Hashing is a crucial component of blockchain technology that ensures the integrity and security of data stored in the chain. The use of hashing in blockchain technology ensures that data in the chain cannot be tampered with and that each modification to the data results in a different hash being created.
Furthermore, the use of a nonce in the hash function, as well as the linking of the hash of each block to the hash of the previous block, results in a chain of blocks that is extremely difficult to change. The notion of hashing is also applied in other emerging technologies such as distributed file systems and distributed databases, demonstrating its adaptability in ensuring data integrity in a decentralized setting.
I hope you found this article useful.
Thank you for reading.