Digital signatures have become an essential tool for assuring the validity and integrity of electronic documents and transactions. They use a pair of keys to encrypt and decrypt data and are based on complicated mathematical procedures. Digital signatures have become increasingly vital for protecting sensitive information and guaranteeing secure transactions as e-commerce and online communications have grown in popularity.
In this article, we will dive deeper into the world of digital signatures and discuss the mechanics of how they work, the different types of digital signatures, and their different use cases. We will also go through the security and vulnerabilities of digital signatures, as well as the need of employing trustworthy third parties for identity verification.
Introduction
Digital signatures are a technique of data encryption that uses a mathematical algorithm to create a unique, unchangeable code. This code, or "signature," is then used to validate the document's validity and ensure that it has not been tampered with. Digital signatures are also used for non-repudiation, which means that the signer cannot deny signing the document.
How digital signatures work
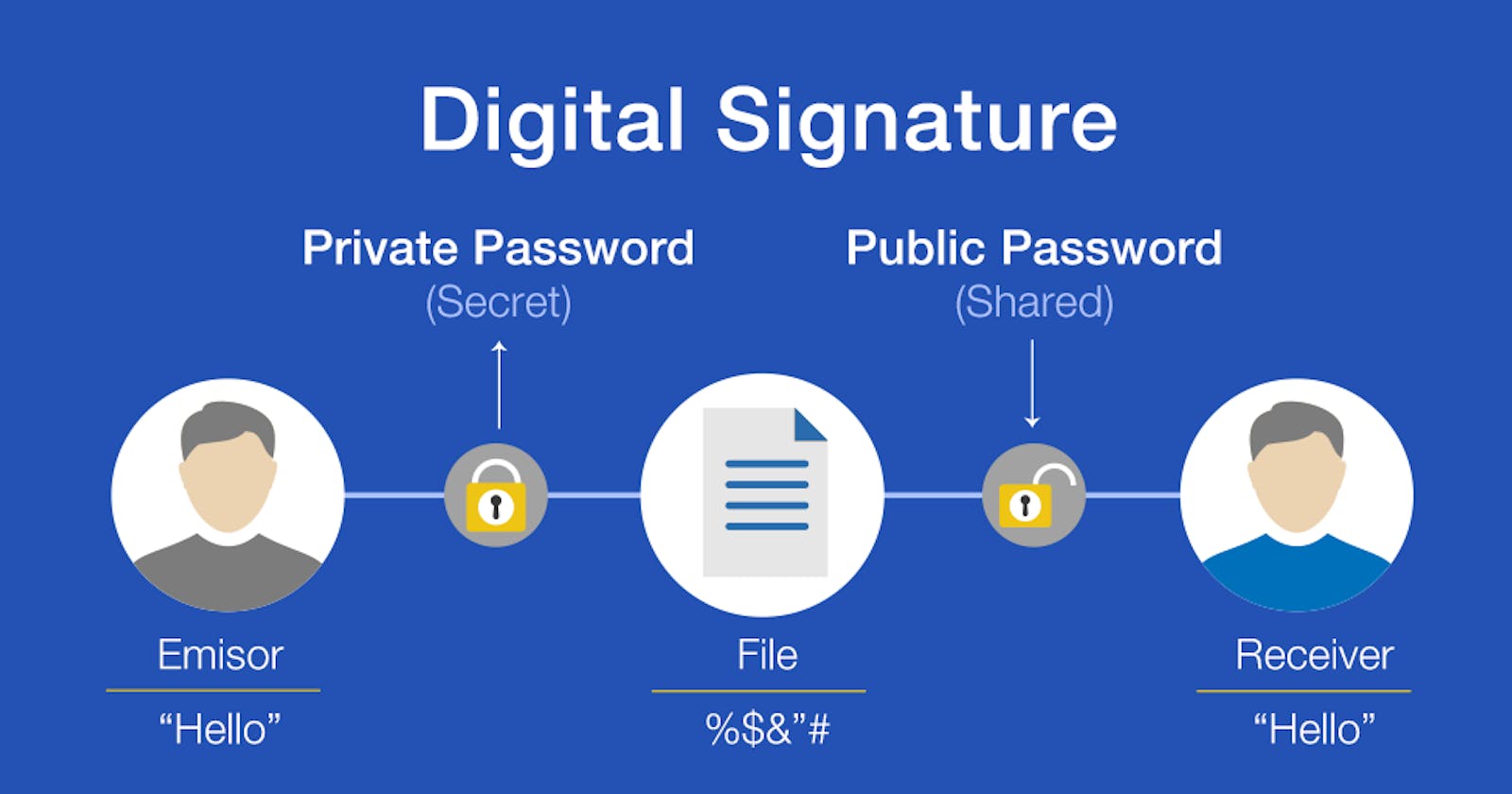
Digital signatures are based on public key cryptography, which encrypts and decrypts data using a pair of keys. The owner of the digital signature keeps one key, known as the private key, confidential, while the other key, known as the public key, is made available to others.
When a document is digitally signed, the private key is used to encrypt the hash, which is a unique code that represents the contents of the document. The resulting digital signature, along with the public key, is then attached to the document to form a signed document. A recipient can use the public key to decrypt the digital signature and compare the resulting hash to the contents of the document to validate its authenticity. If the two match, the document is regarded as authentic and free of manipulation.
Types of digital signatures
Simple digital signature: This is the most basic type of signature and is used to guarantee the authenticity of a document. It encrypts the document's hash with a single private key and offers no protection against alteration.
Digital signature with certification: This type of signature is similar to a simple digital signature, but it also includes a certificate that verifies the owner's identity. This certificate is issued by a trusted third party, such as a certificate authority (CA), and is used to verify that the signature belongs to the person or organization to whom it claims.
Digital signature with timestamping: This type of signature includes a timestamp that verifies the date and time that the document was signed. This is useful in situations where the document's authenticity needs to be verified at a later date, such as in legal proceedings.
Digital signature with document recovery: This type of signature includes a mechanism for recovering the original document in case it is lost or damaged. This is useful in situations where the document is critical and needs to be preserved for future use.
Use Cases of Digital Signatures
Electronic contracts: Digital signatures are commonly used to sign electronic contracts, such as rental agreements and purchase orders. This ensures that the contract is authentic and has not been tampered with. It provides a way for the parties to the contract to confidently verify the identity of the other party and the contents of the contract, which can help to prevent fraud and disputes. Additionally, digital signatures can be used to automate the contract execution process, reducing the need for manual signatures and making it easier for parties to sign and access the contract remotely.
Secure communications: Digital signatures are used to secure communications, such as email and instant messaging. They are used to ensure that the message is authentic and has not been tampered with during transit.
E-commerce: Digital signatures are used in e-commerce to secure online transactions and protect sensitive financial information.
Government: Digital signatures are used by government agencies to secure online transactions and protect sensitive information.
Security and Vulnerabilities of Digital Signatures
Common attack methods
Digital signatures are vulnerable to attacks, such as man-in-the-middle attacks, in which a malicious actor intercepts the communication between two parties and alters the document or signature.
Protecting against attacks
To protect against these attacks, it is important to use secure methods for transmitting and storing digital signatures and to regularly update software and systems. This includes using secure protocols for communication, such as HTTPS, and implementing proper security measures for storing and managing private keys.
Trusted third parties
Another important aspect of digital signature security is the use of trusted third parties, such as certificate authorities (CAs), to verify the identity of the signature's owner. CAs are organizations that are trusted to verify the identity of individuals and organizations, and they issue digital certificates that are used to validate digital signatures. When using digital signatures, it is important to use a CA that is reputable and has a good track record of security.
Conclusion
In conclusion, digital signatures are an important tool for ensuring the authenticity, integrity, and non-repudiation of electronic documents and transactions.
They have a wide range of use cases in various industries, and it is important to use secure methods for transmitting and storing digital signatures and to use trusted third parties for identity verification.
As technology and cyber threats continue to evolve, it is important to stay informed and up-to-date on best practices for digital signature security. It is also important to remember that digital signatures, while useful, are not foolproof and need to be used in conjunction with other security measures to provide the best protection.
I hope you found this article useful.
Thank you for reading.